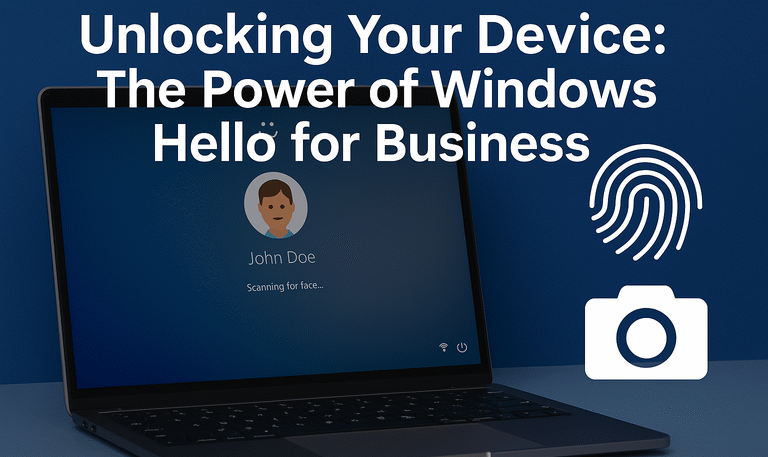
Unlocking Your Device: The Power of Windows Hello for Business
In a world where cyber threats grow more sophisticated by the day, protecting business data and systems has never been more crucial. According to the 2024 cybersecurity report by Canadian Internet Registration Authority (CIRA), 44% of organizations have experienced a cyber attack in the last 12 months. While organizations often implement multi-factor authentication (MFA) for […]