Many businesses still struggle with their Microsoft 365 MFA setup and are vulnerable to credential theft and account takeover. Multi-factor authentication (MFA) adds a second verification layer beyond the password, such as a phone notification or hardware key. This dramatically reduces risk and protects your organization from account compromise and data.
In this 7-step guide, you will learn how to optimize MFA in Microsoft 365. By the end of this guide, you will have a secure Microsoft 365 login for all users.
Step 1: Migrate from Legacy MFA to Authentication Methods Policy
Microsoft is retiring Legacy per-user MFA on September 30, 2025, in favor of the unified Authentication methods policy in Microsoft Entra. Therefore, it is essential to migrate from legacy MFA to the unified Authentication Methods policy in Microsoft Entra ID.
Follow the steps below to perform the migration:
- In the Microsoft 365 admin center, go to Entra ID → Authentication methods → Policies.
- Under Multifactor authentication, enable the same methods (such as Authenticator app push, SMS, passkeys) targeting All users.
- Return to Users → Multi-factor authentication (legacy), disable all legacy settings, and clear legacy SSPR options.
- In Manage migration, switch the state to Migration complete, so only the new policy applies.
Completing this migration ensures your Microsoft 365 MFA setup uses the modern, more flexible policy engine rather than the retiring legacy portal.

Step 2: Define Your MFA Strategy
Not all MFA methods are equal, as some resist phishing better than others. Therefore, Microsoft classifies methods into three strengths:
- Basic MFA: Password + SMS or app notification (medium assurance).
- Passwordless MFA: Windows Hello, passkeys, certificate-based (higher assurance).
- Phishing-resistant MFA: FIDO2 security keys, Windows Hello biometrics (highest assurance)
As an MFA best practice, avoid SMS/voice where possible, as these can be intercepted. Instead, aim to enable multi-factor authentication Microsoft 365 using passwordless or phishing-resistant methods on corporate devices. This strategic layering of Microsoft 365 authentication methods greatly reduces the risk of credential theft.
Step 3: Audit Your Environment
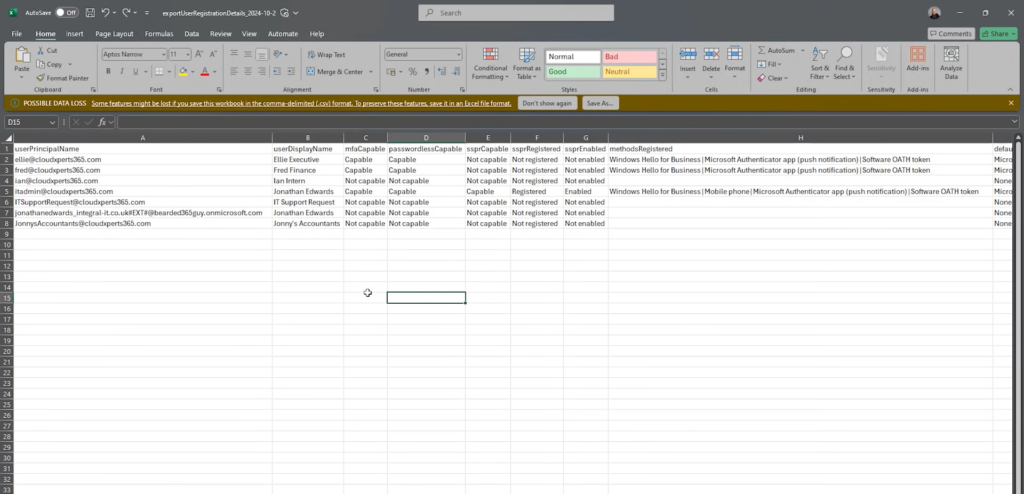
Before enforcing policies, understand who in your tenant has or lacks MFA. In the Entra admin center, navigate to Protection → Authentication methods → Monitoring → User registration details and download the CSV report. The report shows for each account:
- MFA capable/configured
- Passwordless capable/configured
- Registered methods and default method
Use this data to identify users with no MFA, admins lacking phishing-resistant methods, and guest accounts needing enrollment. This audit becomes your action plan for targeted outreach.
Step 4: Drive User Registration
With your audit in hand, launch an MFA registration campaign. There are two approaches to do so:
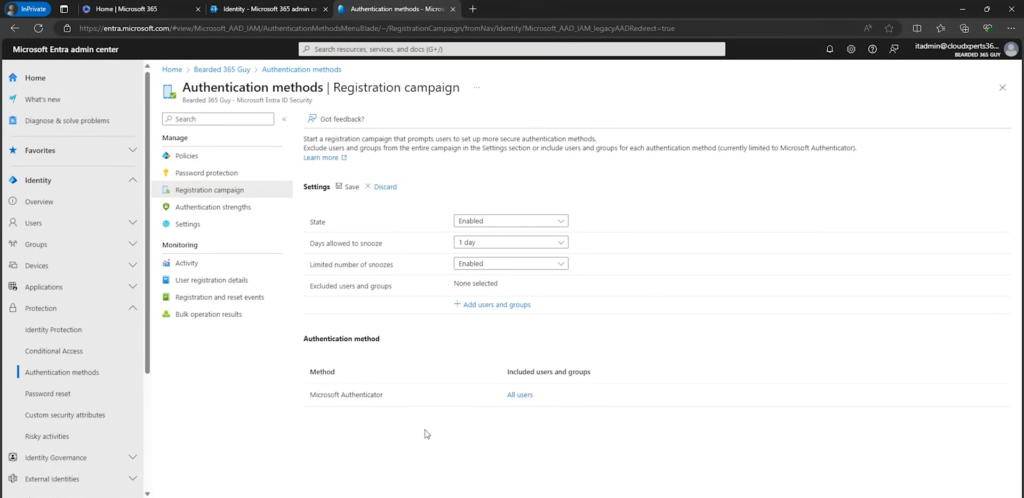
- Entra Registration Campaign: Under Authentication methods → Registration campaign, enable the campaign, set snooze limits, and include all users to prompt them at sign-in.
- Manual Email Campaign: Send personalized emails explaining why MFA matters, how to enable multi-factor authentication Microsoft 365, and links to short how-to videos.
Track progress in your spreadsheet. Mark users green once they complete registration. This ensures you secure Microsoft 365 login by getting everyone enrolled.
Step 5: Enforce MFA via Conditional Access
Conditional Access lets you secure Microsoft 365 login by requiring MFA under defined conditions. To enforce conditional access:
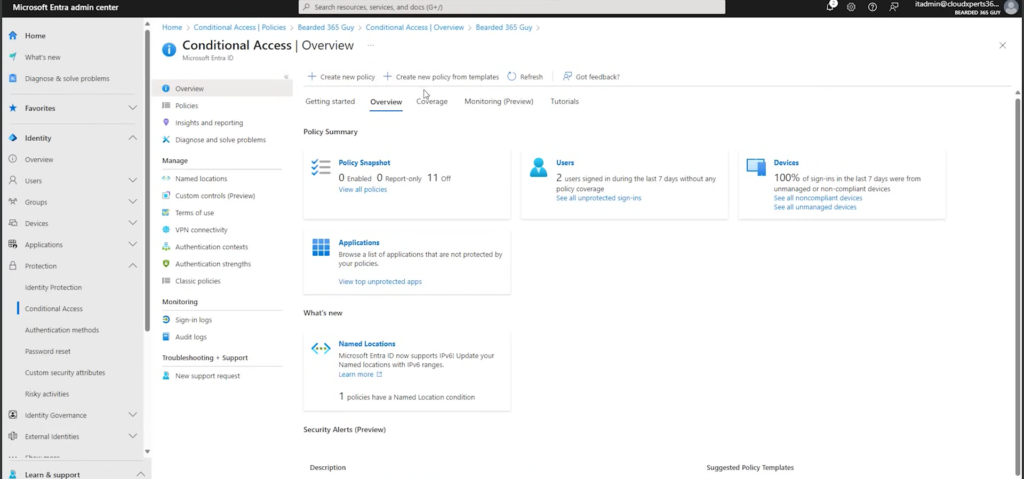
- In Entra admin center, go to Protection → Conditional Access → Policies.
- Use the “Require multifactor authentication for users” template to create a policy for all users; start in Report-only mode to assess impact Microsoft Learn.
- Likewise, apply the “Require multifactor authentication for guest access” template.
- Once validated, switch both policies to On.
These policies ensure every sign-in triggers your Microsoft 365 MFA setup, fully enforcing your strategy.
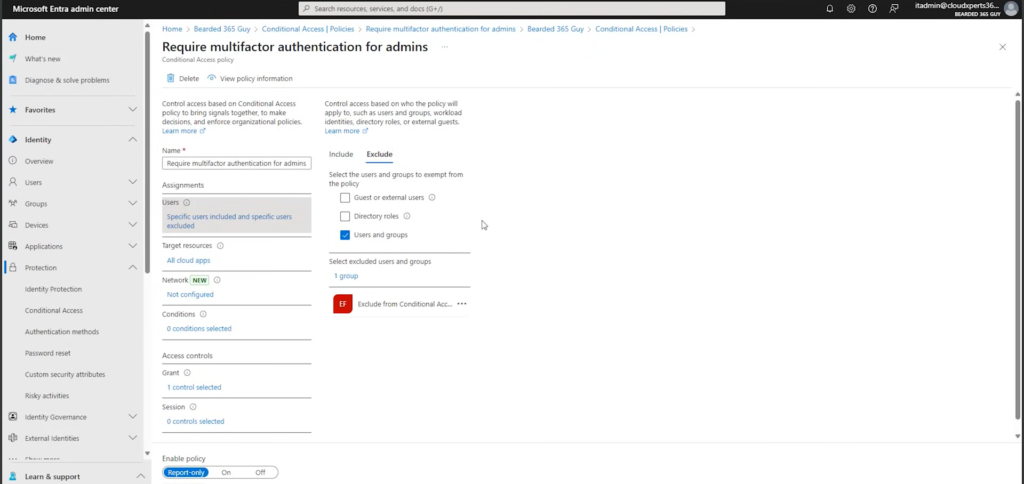
Step 6: Apply Phishing-Resistant MFA for Admins
High-privilege accounts demand stronger controls. Microsoft’s built-in Authentication strengths let you enforce phishing-resistant MFA for admin roles:
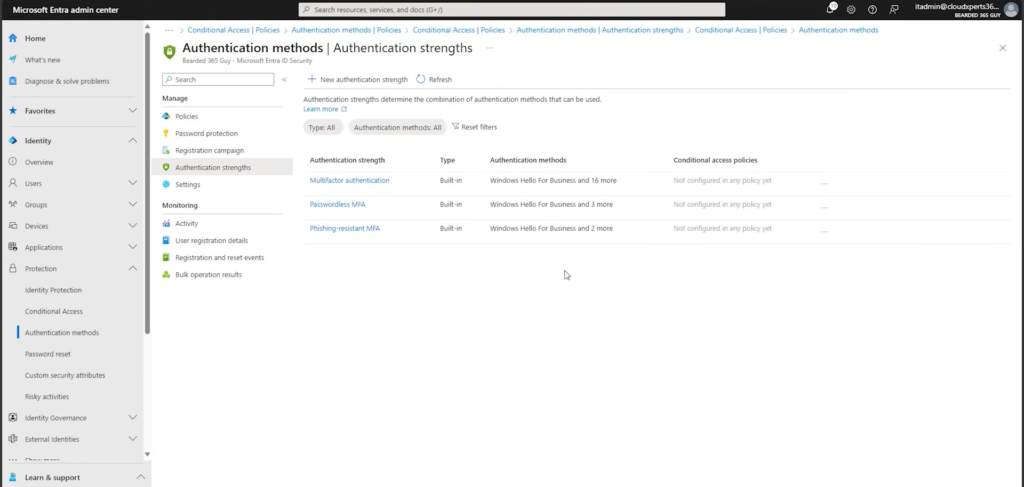
- Go to Authentication methods → Authentication strengths.
- Select the “Phishing-resistant MFA” strength (only FIDO2 keys, Windows Hello, or cert-based methods allowed).
- Create a new Conditional Access policy from the “Require MFA for admins” template. Under Grant controls, choose “Require authentication strength” and select “Phishing-resistant MFA”. Start in Report-only mode, then enable once admin accounts have registered hardware keys.
This ensures privileged roles use only the most secure factors in your Microsoft 365 MFA setup.
Step 7: Configure Emergency Break-Glass Accounts
To avoid a total lockout, establish two emergency access (break-glass) accounts excluded from Conditional Access but still protected by MFA:
- Create accounts under the onmicrosoft.com domain and assign the Global Admin role.
- Add them to a security group (e.g., ExcludeFromCA) and exclude that group from your Conditional Access policies.
- Register FIDO2 hardware security keys (e.g., YubiKey) via aka.ms/mysecurityinfo. Configure the FIDO2 GUID under Entra ID → Authentication methods → FIDO2 Security Key Settings.
Store these keys in a secure safe and record PINs in a password manager. These accounts serve only for emergency use.
MFA Best Practices for Microsoft 365
Implementing a robust MFA strategy requires more than just turning on extra factors. It demands careful planning, deployment, and ongoing management to maximize security and user experience. Below are some effective MFA best practices for Microsoft 365:
- Optimize Reauthentication Frequency: Configure sign‑in frequency and session lifetimes to balance security and usability; excessive prompts can train users to bypass or ignore MFA challenges, so apply shorter lifetimes only for high‑risk scenarios.
- Leverage Combined Registration for MFA and SSPR: Use the unified security information registration experience so users can enroll for MFA and self‑service password reset simultaneously, reducing friction and support calls.
- Deploy the Authenticator App with Number Matching: Push deployment of the Microsoft Authenticator app via Intune or other MDM and enable number matching to mitigate “push‑bombing” attacks where adversaries send repeated prompts.
- Apply Conditional Access to All Cloud Apps: Ensure every app is covered by at least one Conditional Access policy—ideally targeting “All cloud apps”—so on‑boarding new services automatically inherits MFA requirements.
- Start in Report‑Only Mode: Before enforcing new Conditional Access policies, run them in report‑only to identify unintended blocks and adjust scopes, minimizing user disruption when you switch to enforcement.
- Embrace the Principle of Least Privilege: Grant only the minimum access necessary; combine role‑based access control (RBAC) with MFA to reduce attack surfaces, especially for privileged roles.
- Favor Phishing‑Resistant and Passwordless Methods: Prioritize FIDO2 security keys, Windows Hello for Business, and passkeys over SMS or voice calls, since these methods resist phishing and man‑in‑the‑middle attacks more effectively.
Regularly review your MFA configurations, authentication methods, and Conditional Access policies to adapt to evolving threats and ensure continuous protection.
Read more: Safeguard Your Microsoft 365 Tokens From Sneaky Thieves!
Conclusion
A comprehensive Microsoft 365 MFA setup not only meets compliance requirements but also dramatically reduces the risk of unauthorized access. With migrating off legacy MFA, defining a strong MFA strategy, auditing your tenant, driving user registration, leveraging Conditional Access, enforcing phishing-resistant methods for administrators, and establishing secure break-glass accounts, you implement strong MFA best practices and Microsoft 365 authentication methods that stand up to modern threats. Begin your Microsoft 365 MFA setup journey today and secure Microsoft 365 login across your organization.
If your organization needs expert support implementing Microsoft 365 MFA setup or enhancing your security posture, Sun IT Solutions is here to help. We specialize in configuring multi-factor authentication, managing secure Microsoft 365 login environments, and applying best practices to protect your users and data. Our team ensures your Microsoft 365 environment is both secure and user-friendly.
Get in touch with us to learn how we can safeguard your business today.




